Phishing
Phishing (play on the word 'fishing') is a type of social engineering attack where a malicious user creates a seamless copy of another website, with the idea of stealing credentials (or FISHING for them, hence the name). It is by far the most common 'cybercrime' [1]. Since Covid began, the number of phishing websites detected has drastically increased, as many people began working from home [2]. Since quarter 1 of 2020 there has been an almost 800% increase in phishing websites [2]. Phishing is also the leading cause of ransomware infections [3] Younger adults are more likely to receive and fall victim to such scams [4] (though the study excludes those younger than 24). Bare in mind that these are reported cases. From personal experience phishing is so prevalent that it is often under-reported.
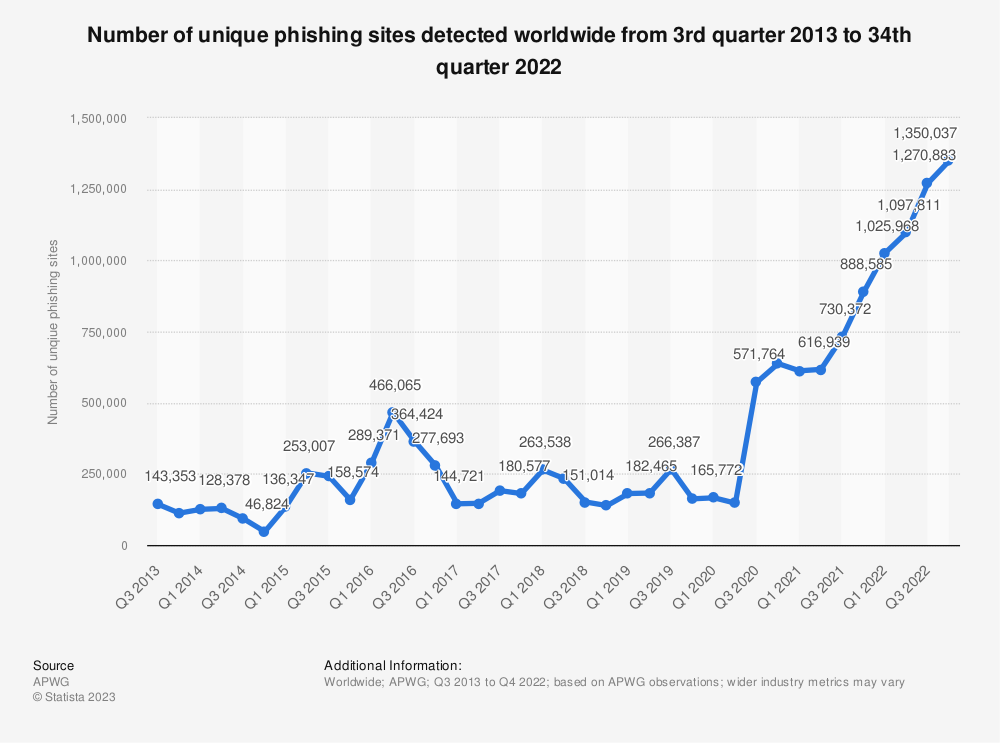
Despite its prevalence (and the sheer number of victims), I feel phishing is not mentioned enough when discussing security. VPN ads talk about malicious third parties eavesdropping on your traffic. Movies and media present cyber attacks as involving some complex cracking of security measuers. Indeed these do happen [5], but the most common attacks target humans. The reality is our cryptographic protocols have become highly sophisticated and proven secure. Unless a mistake is made in their implementation, there is almost 0 chance your passwords will be cracked in transit. Exploits arise from oversights or bugs in development and are hard to find and usually patched relatively quick. It is too expensive and too difficult to target the computer itself. However, the most vulnerable part are the people using it. This is what social engineering attacks target. They aim to exploit the negligence or incompetence of people to acquire access into a system. Phishing, specifically, aims to obtain user credentials by creating a fake login page for a given platform. The victim, who has opened the fraudulent page, enters their details, and is forwarded to the real website. Often, to them, there is no indication they were on a fake website. However, the username and password were in reality sent to the attacker. And considering people tend to reuse passwords on different platforms and even for work accoutns [6], obtaining this information is a very serious security risk.
So why isn't it mentioned on the front page of every coursebook? Probably because it is so simple that it is stupid. It feels almost not worth thinking about. "I will never fall for this!"... But the wheel is tipped over by small stones.
My hope with this article is to warn you about phishing and teach you how to avoid becoming victims to it. And what is the best way to defend? It is to learn to attack. That way you will know all the tricks that can be used to successfully execute such an attack.
How to Phish
Cloning the website is not particularly difficult. Websites that load their content dynamically can still be cloned. After all, browsers need to at some point display everything to the user and for that they need to have all the relevant content stored locally. Even simpler - one can simply make a website that looks like the targetted one. Tools exist a-plenty to make this process as easy as clicking a button. Here I have taken the code generated by ZPhisher for the Facebook login page: theworkerthread.com/demo/fakebook. I have obviously modified it a bit so that if an unsuspecting person stumbles upon it they still realise it is a fake page (plus hopefully my website doesn't get banend for that :D). Normally, everything you do on the website will be sent to the attacker of the server. On this page I have removed this functionality to ensure your safety.
Next comes the difficult part. You have to somehow get the user to click on the link believing it to be facebook. If you just sent them this ugly looking theworkerthread.com/demo/fakebook they will immediately realise it is a scam. So you have to be smart. One option is to mask the link like this: https://[email protected]/demo/fakebook.
This is a bit harder to see now. There is INDEED a facebook.com in the beginning part of the URL and some people may not look too closely at it. But the ugly looking @ might catch your attention. What this URL actually does is send a username "facebook.com" to the page theworkerthread.com/demo/fakebook. The page then simply loads the fakebook design.
There are hunderds of other ways one can obfuscate the original URL to make it seem like the legitimate one. Typosquating is another very common one. Attackers will buy domains that are similar to the targetted website, but with some mistake in spelling or some characters replaced. For example, for facebook, one can buy the domain "faceobok.com" (which Meta has already bought to prevent such an attack). I tend to sometimes not see misspellings like that. Another way is to replace letters that appear similar - for example switching "m" with "rn", which under certain fonts may fool someone not paying too much attention. And with the internalised domain names, which allow non-ASCII characters, attackers can simply replace letters with ones from another alphabet that look identical. The latin "a", "c", "o", etc. look identical to the Cyrilic "а", "с", "о"... Consider the url: https://www.facеbook.com
Other cheaper alternatives exist. QR-codes are a big offender. The victim scans the QR code and is taken to the page, without paying too much attention to the URL, which on a phone screen is too small to read fully.

Then comes the psychological aspect. You send the victim the link via email, instant messaging, SMS, and so on, and you attach with it some text which will make the user click on the link urgently. 2 years ago many of my friends fell for such a phishing scam over instagram. They would receive a message from a friend saying "This looks a lot like you [malicious link]". They would click on it, enter their credentials, and bahm. Many users fell victim to such attack during Covid - receiving emails or SMSs that they need to check their results or something with a malicious link.
How to escape the Phish
Phishing as an attack has existed for well over 20 years, and yet no good protection exists. I tried some of the extensions that were supposed to "detect scam websites", but most of them didn't work all the time. Other solutions were often paid, so I did not evaluate them.
In truth, the system itself is made secure enough. The problem is not a technological one. The whole attack hinges on human error and negligence. Some advices say that you should check the SSL certificate of the website to verify its identity, but no reasonable person would do that ever. At best - be smart about it. If you are suddenly taken to a login page, which you did not expect to be on (especially if you were JUST using the website) - stop and think. Take a quick look at the URL. Most phishing scams do not have the resources to invest in domains. Then click around. These scams are usually quite simple and have a very specific user-flow in mind. If you suddenly start interacting with elements you were not expected to, chances are the illusion will break. And the silver bullet - open a new window and login to the required service by entering the url for it yourself.